Reverse Engineering
Nested Rev (150 Pts)
Description
-
Solution

Using ghidra for open the binary file and go to the main function

There are lots of if statement which if we order the variables it will produce flag, but i’m too lazy to do it. So here i am using angr to automate solving that binary.
Finding address of main function
Finding instruction for load string “Voila!!! You Got It” from memory using gdb.
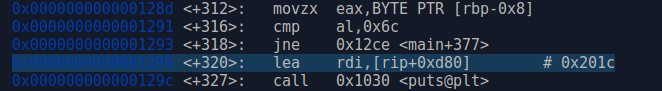
After that write a program for find the correct value automatically using angr.
and here is the result.
Flag : d33p{y0u_r3v3rs3d_1t_w3ll}
SkipMe (200 Pts)
Description
-
Solution
Open the binary using ghidra and go to the main function

In this challenge we need to change the value of our computer name,os,cpuid to the correct value like in strcmp argument and in the end if our values are correct the program will run finish function. So like the title of challenge “SkipMe” , we can skip all those checks and directly call finish function.


Flag : d33p{f51579e9ca38ba87d71539a9992887ff}
0xKEY (300 Pts)
Description
-
Solution

Open the binary using ghidra and go to the main function

I think this challenge is broke, because we can easily knowing the flag by using ltrace command (because there is strcmp function which compare string and we can find out the argument of strcmp using ltrace command).

If there is no strcmp function we can examine the address of secret like this for find out the flag.



Flag : d33p{jnhFClg2sv3uaBBxs}
Down (300 Pts)
Description
-
Solution

Open the binary using ghidra

Nothing helpful, so here i decide to run the file and here is the result.
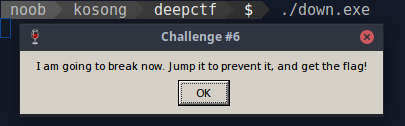
After clicking ok the program will close, but here we know some string stored on that executable , so the next step is try to examine defined string on that executable.
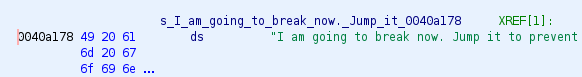
Using the address for that string we can find the reference to that address which may be the address of main function.

Lets move to assembly tab instead of pseudocode tab to be more obvious.

from the instruction we know that the program after calling message box will call FUN_004012c0() which is calling GetTickCount function and the next instrucion is INT (interrupt) 3 which is intended for calling the debug exception handler and this instruction make the program break. There area many int 3 instruction after calling FUN_004012c0() and then something like garbage after the last int 3 instruction.

Here i try to convert it to assembly instruction and here is the result

There are some jump instruction and the last jump instruction lead to the flag.

So here my solution is changing the assembly instruction int3 to nop so the program can continue to the next instruction and lead to the message box with flag on it.


And then run the file to get the flag


Flag : d33p{ww.canabalt.com}
Wacha Wachin (500 Pts)
Description
-
Solution

At the beginning i thought the challenge was about reversing the encrypted pdf file , but it didn’t,it was even worse :) . Here is the contents of the pdf file.
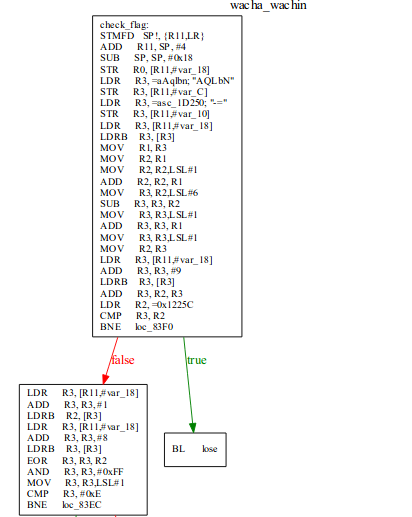


That is assembly on arm architecture, here I analyze these instructions manually .
Some arm assembly instruction cheat sheet
Here i will say set of instruction per box as section, so start from the first section
The next step is writing script for bruteforcing the value per section.
On the first section i got exact value for flag[0] and flag[9].
On the second section i got many possibilities for flag[1] and flag[8] , so we keep the value and go to third section.
On third section i failed to find value for flag[8] ( i think because i fail to implement umull instruction ) so i decided to go to fourth section.
On fourth section i got exact value for flag[1] and on the second section we know that flag[1] and flag[8] in pairs , so from fourth section i got value for flag[1] and flag[8]. Fifth section is the clearest section,flag[7]=’i’ .
The last is loop section , on loop section we will get values for flag[2] until flag[6]. Here is my script i used to get the flag using bruteforce method.
or you can see the full script include my comment while debugging.
Flag : d33p{b3lla_ci40}
Last updated